Stay Compliant, Stay Secure with Cybersecurity Services!
Protect your business with Expert Cybersecurity Services by Dual Layer IT. Every business has unique threat landscape, and we go through every detail to make sure there is compliant Cybersecurity solution in place for protection of IT systems.
- NIST Cybersecurity Framework Compliance
- Proactive Emergency Response
- 24/7 Threat Monitoring & Alerts
- Tailored for Business Requirements
- Centralized Patches & Updates Management
Your Partner in Cybersecurity Management
Dual Layer IT provides managed cybersecurity services with a thorough approach to assessing cybersecurity risks for clients. Industry-leading solutions are implemented to protect clients’ IT infrastructure and data environments. Collaboration with clients helps identify, prioritize, and execute security controls.
Alignment with cybersecurity IT standards such as NIST, COBIT, CIS controls and Zero Trust Architecture assists customers in achieving their cybersecurity goals through a well-managed process. With over 20 years of experience within IT and cybersecurity field, Dual Layer is well placed to manage client IT requirements.
Managed Security Services
24/7 monitoring and real-time threat detection, management with industry best SIEM, XDR, EDR Solutions
Managed Endpoint Security
Protection, Patching, Monitoring and Alerting for devices, including laptops, desktops, and IoT
Cloud Security
Safeguarding data and systems in AWS, Azure, and Google Cloud environments.
Network Security
Secure Firewall, Routers, Switches Configuration and Management, VPN security, and gateway filtering, IPS and IDS solutions
Cybersecurity Training
Train your whole organization to build layered defenses. Fully managed online training
Regulatory Compliance
Expertise to meet regulatory standards like GDPR and Regulatory bodies such as SFC, MAS and SEC
Cybersecurity Audit
Align IT and process with NIST, COBIT and CIF control guidelines. Gap analysis, Risk Mangement and Policies Development
Vulnerability Scanning
Find issues, missing configurations and zero day threats with comprehensive and continuous internal or external assets scanning.
Pen Testing
Comprehensive Pen Testing services with full life cycle management of the Pen Testing process. Professional Remediation and Reporting Service
Need Regulatory Compliant Audits?
Cybersecurity for Regulated Businesses in Hong Kong
Dual Layer IT provides consulting and Cybersecurity Assessment to local businesses need to comply with cybersecurity regulatory framework from SFC or related local bodies. Check out our comprehensive service mapping for VATPs aspiring to get licensed.
Why Cybersecurity Matters Now More Than Ever
43% of cyberattacks target small businesses.
A cyberattack occurs every 39 seconds.
The average cost of a data breach is $4.35 million
FAQ
Why is cybersecurity important for businesses?
Cybersecurity protects sensitive data, financial assets, and operations from cyber threats like hacking, ransomware, and phishing. Without it, businesses risk financial loss, reputational damage, and legal penalties. Dual Layer IT provides 24/7 monitoring, penetration testing, and compliance support to keep companies secure.
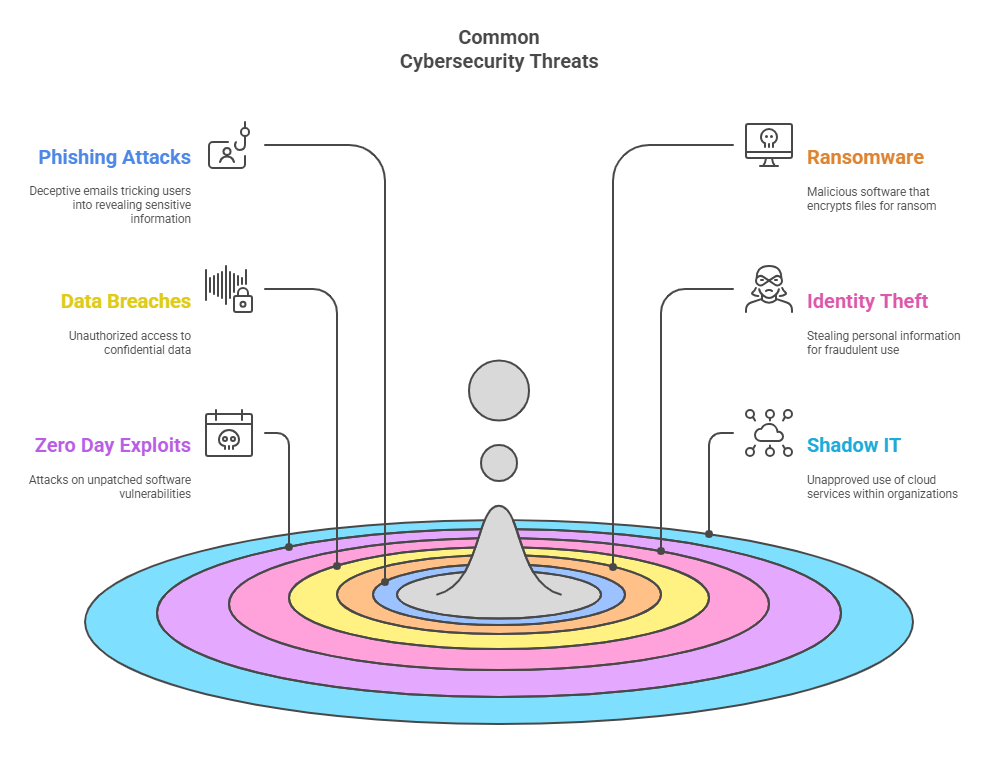
What are the biggest cybersecurity threats today?
Common threats include:
- Phishing – Fraudulent emails stealing credentials.
- Ransomware – Malware encrypting files for ransom.
- Zero-day exploits – Attacks on unknown vulnerabilities.
- Insider threats – Employees misusing data access.
- DDoS attacks – Disrupting services by overwhelming networks.
Dual Layer IT offers threat detection, endpoint protection, and security training to counter these risks.
How can businesses improve their cybersecurity?
Key steps include:
- Using multi-factor authentication (MFA).
- Updating software to patch vulnerabilities.
- Deploying firewalls and endpoint security.
- Conducting penetration testing.
- Training employees on cybersecurity awareness.
Dual Layer IT provides customized security solutions and compliance support.
How can businesses ensure cybersecurity compliance?
Compliance with standards like GDPR, ISO 27001, and NIST ensures data protection and regulatory adherence. Businesses can achieve this through risk assessments, security audits, and policy implementation.
Dual Layer IT provides expert guidance and compliance support.
What is penetration testing, and why is it important?
Penetration testing simulates cyberattacks to uncover vulnerabilities before hackers do. It helps businesses strengthen defenses, meet compliance requirements (e.g., GDPR, ISO 27001), and reduce risks.
Dual Layer IT offers professional Pen testing and remediation strategies.
Why is 24/7 cybersecurity monitoring essential?
Cyber threats can strike anytime, making real-time detection critical. 24/7 monitoring provides:
- Instant threat detection and response.
- Continuous log analysis for suspicious activity.
- Minimized downtime and risk exposure.
Dual Layer IT’s managed security services use SIEM, XDR, and EDR solutions to protect businesses around the clock.
Our Work
Advanced Threat Detection and Response System
Overview
Amid increasingly sophisticated cyber threats, our team developed and deployed an Advanced Threat Detection and Response System for a client in the finance sector. This comprehensive solution was designed to identify, analyze, and mitigate potential security breaches in real-time, protecting sensitive data and ensuring the integrity of the client's digital assets.
Key Features
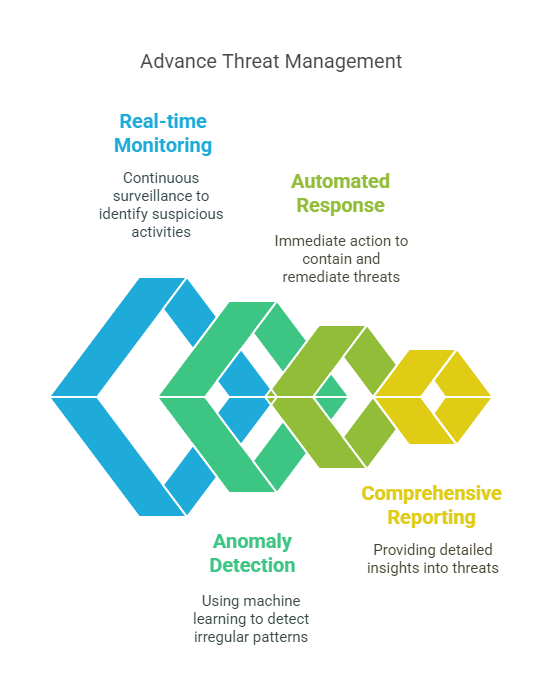
- Real-time Monitoring: Continuous surveillance of the network traffic to identify suspicious activities.
- Machine Learning Algorithms: Utilization of advanced machine learning techniques to detect anomalies and potential threats.
- Automated Response: Immediate containment and remediation of identified threats to prevent further damage.
- Comprehensive Reporting: Detailed reports and analytics to provide insights into the nature and origin of threats.
Achievements
By implementing this system, the client significantly reduced the risk of cyber attacks, minimized the impact of security breaches, and enhanced their overall cybersecurity posture. The project demonstrated success with a notable reduction in incident response times and improved threat detection accuracy.
Secure Cloud Infrastructure
Overview
As businesses increasingly migrate operations to the cloud, securing cloud environments is critical. For a technology company, we developed and implemented a Secure Cloud Infrastructure project. This project focused on creating robust security frameworks and best practices to safeguard the client's cloud-based data and applications from unauthorized access and cyber threats.
Key Features
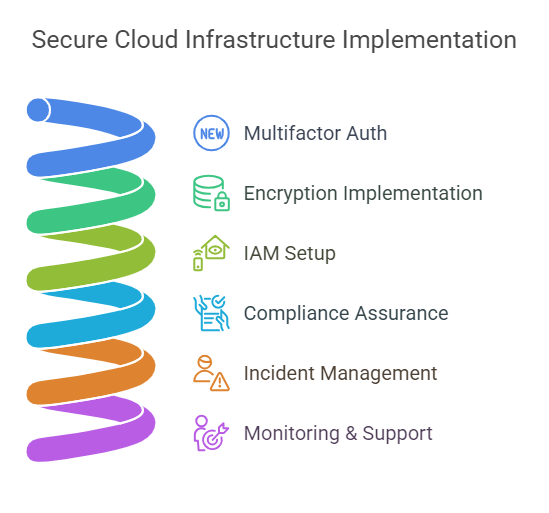
- Encryption: End-to-end encryption of data to ensure confidentiality during transmission and storage.
- Identity and Access Management (IAM): Implementation of granular access controls to manage user permissions and authentication.
- Continuous Compliance: Ensuring that cloud environments adhere to industry regulations and standards.
- Incident Management: Proactive identification and resolution of security incidents through automated tools and processes.
Achievements
The Secure Cloud Infrastructure project enabled the client to confidently leverage the benefits of cloud computing while maintaining robust security measures. By adopting these security frameworks, the company reported enhanced data protection, reduced compliance violations, and increased trust in their cloud services.
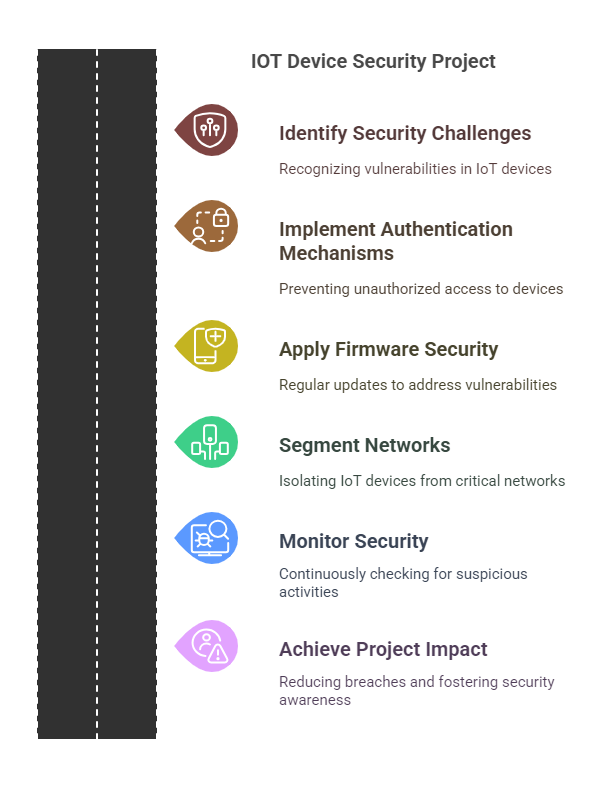
IoT Device Security Enhancement
Overview
The proliferation of Internet of Things (IoT) devices introduces new security challenges, as these devices often lack robust security measures. For a manufacturing client, we developed and implemented the IoT Device Security Enhancement project. This project focused on securing the client’s IoT ecosystem by addressing vulnerabilities and implementing strong authentication protocols.
Key Features
- Device Authentication: Implementation of strong authentication mechanisms to prevent unauthorized access to IoT devices.
- Firmware Security: Regular updates and patches to address known vulnerabilities in IoT device firmware.
- Network Segmentation: Isolation of IoT devices from critical networks to minimize potential attack vectors.
- Security Monitoring: Continuous monitoring of IoT devices for suspicious activities and potential threats.
Achievements
Through the IoT Device Security Enhancement project, the client achieved greater control over their IoT ecosystem, resulting in a significant reduction in security breaches and unauthorized device access. The project also fostered a culture of security awareness and best practices among IoT device manufacturers and users.
Why Businesses Trust Dual Layer IT for Cybersecurity Solutions

Over 20 Years of Expertise
Decades of experience in cybersecurity and IT infrastructure projects regionally ensures deep knowledge and proven strategies.
Skilled & Experienced Team
Dual Layer IT is staffed by a team of seasoned professionals who bring a wealth of knowledge and experience to the table. Their expertise spans across multiple facets of IT and qualified in many different IT domains.





24/7 Service Desk Support
Our teams provide professional support services with customer satisfaction and always available to help. We understand that IT issues can arise at any time, and our support service ensures that help is always just a phone call away.
Client Centric Approach
At the heart of Dual Layer IT’s philosophy is a client-centric approach. We prioritize understanding the unique needs of each client and strive to build long-term, collaborative relationships. This focus on client satisfaction ensures that we consistently meet and exceed expectations. Personalized support, ensuring all client concerns are addressed with care and attention.

Customised Solutions
Recognizing that no two businesses are alike, Dual Layer IT offers tailored solutions that meet the specific needs and goals of each client. Whether it’s designing a robust cybersecurity solution or implementing cloud solutions, we ensure that every strategy is customized to deliver maximum value.
Cutting Edge Technology
Staying ahead of the curve is crucial in the IT industry, and Dual Layer IT is committed to leveraging the latest technologies. By utilizing cutting-edge tools and solutions, we ensure that their clients benefit from the most advanced and effective IT services available. Our Teams are always busy with research, development and testing new solutions and features which benefit our clients.

Strong Security Culture
In an era where cyber threats are a major concern, Dual Layer IT places a strong emphasis on security and compliance. We implement comprehensive security measures to protect our clients' data and systems. From advanced firewalls to regular security audits, we leave no stone unturned in safeguarding business assets.
Compliance and Regulatory Adherence
Navigating the complex landscape of IT compliance and regulatory requirements can be challenging for businesses. Dual Layer IT helps clients stay compliant with industry standards and regulations, reducing the risk of legal issues and fines. We work to help our clients meet regulatory requirements and our solutions follow standard IT frameworks such as NIST, COBIT.

Proactive Approach
Dual Layer IT takes a proactive approach to IT management. Rather than waiting for problems to occur, we constantly monitor systems and perform regular maintenance to prevent issues before they arise. This proactive stance minimizes downtime and keeps business operations running smoothly.
Transparency and Accountability
Clear communication and detailed reporting to keep you informed about your cybersecurity performance.
Commitment to Excellence
Treating every issue seriously and delivering solutions with the highest standards of professionalism.
